Cybersecurity breaches leads to numerous problems including destruction of operating systems, disruption of access to information, loss or theft of data and privacy depreciation. Unfriendly security mechanisms can also hinder users from patronising web-based services. Understanding how to configure most of the powerful security mechanisms that are available for protecting users from security breaches and attacks is quite challenging for majority of computer users. Because home users in particular lack adequate knowledge in cybersecurity, they tend to be more vulnerable to cybersecurity threats [1]. Despite the fact that most computer security failures are triggered by user errors, security-related interfaces still tend to be very unclear and unfriendly. There has been a consensus in the computer security research community that usability of cybersecurity is critical to maintaining and improving the security of information systems. However, the human element of cybersecurity is still not well understood hence the design of security with unfriendly user interfaces as a problem persist. A major challenge to addressing the human component of cybersecurity is the lack of reliable behavioural data on users’ online security actions.
In spite of advances in Human-Computer Interaction (HCI) techniques and its wide adoption in evaluating commercial systems/applications, it is only recently that researchers begun applying HCI usability evaluation techniques to security systems [2]. Research shows that there are inherent properties of security that calls for a distinct set of design principles and strategies. Recent trends in computer security research highlights how human behaviour can impact on the usefulness of technical security solutions [3, 4]. The focus of this research therefore is to study and understand people’s security behaviors and actions on the web and how that knowledge can be leveraged towards improving the usability of cybersecurity mechanisms.
The aim is to develop an integrated view of online security-related attitudes and behaviours to facilitate the personalisation of cybersecurity tools. To do this, a mix research approach involving data science and HCI techniques is being adopted for an in-depth analysis of users’ online security behaviour. As part of understanding users’ attitude towards cybersecurity, this research is focusing on the features of web browsers, their inherent vulnerabilities and how users interact with these features for security online. It is expected that the outcome of the research will help in minimising the gap between people and cybersecurity in order to promote more frequent and correct usage of security tools and reduce human errors and dissatisfaction.
The research model is built around all the external variables identified as possible factors influencing perceived risk, perceived ease of use and perceived usefulness of technology in general. People’s perceptions and attitude to personal data are hypothesized to have effect on the adoption and acceptance of cybersecurity tools [5]. Thus the research will explore variables like culture, context of use and user demographics such as age, gender, education and/or income and their influence on people’s attitude towards cybersecurity mechanisms.
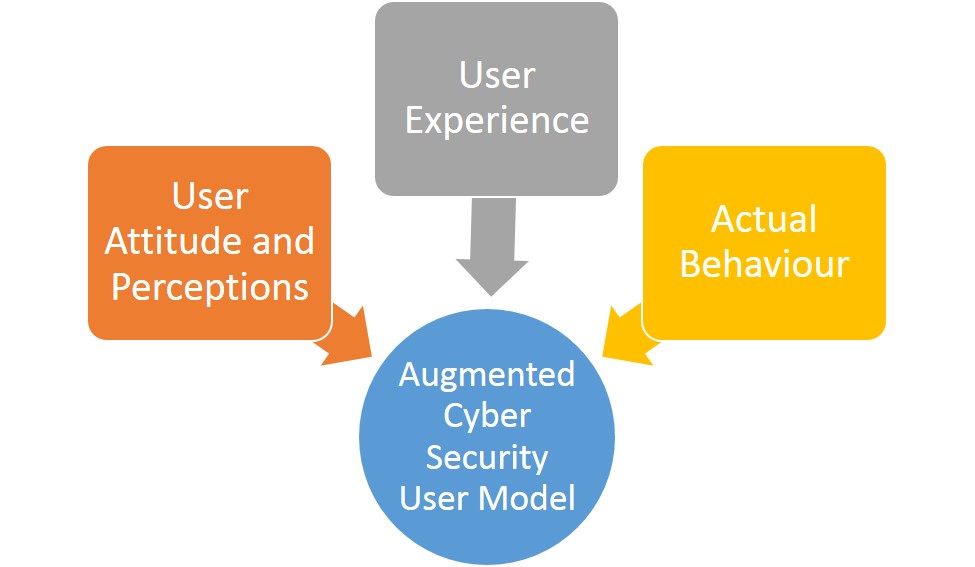
Figure Conceptual framework linking the different facets of the research
This work was carried out at the International Doctoral Innovation Centre (IDIC). The authors acknowledge the financial support from Ningbo Education Bureau, Ningbo Science and Technology Bureau, China's MOST, and the University of Nottingham. The work is also partially supported by EPSRC grant no EP/G037574/1.